Risk Management of the Corporate Information
Governance Risk
Information security solutions tailored to each company. This methodology is based on ISO 27002, which is the Code of Good Practice for the Management of Information Security (formerly ISO / IEC 17799: 2005).
Information security management system
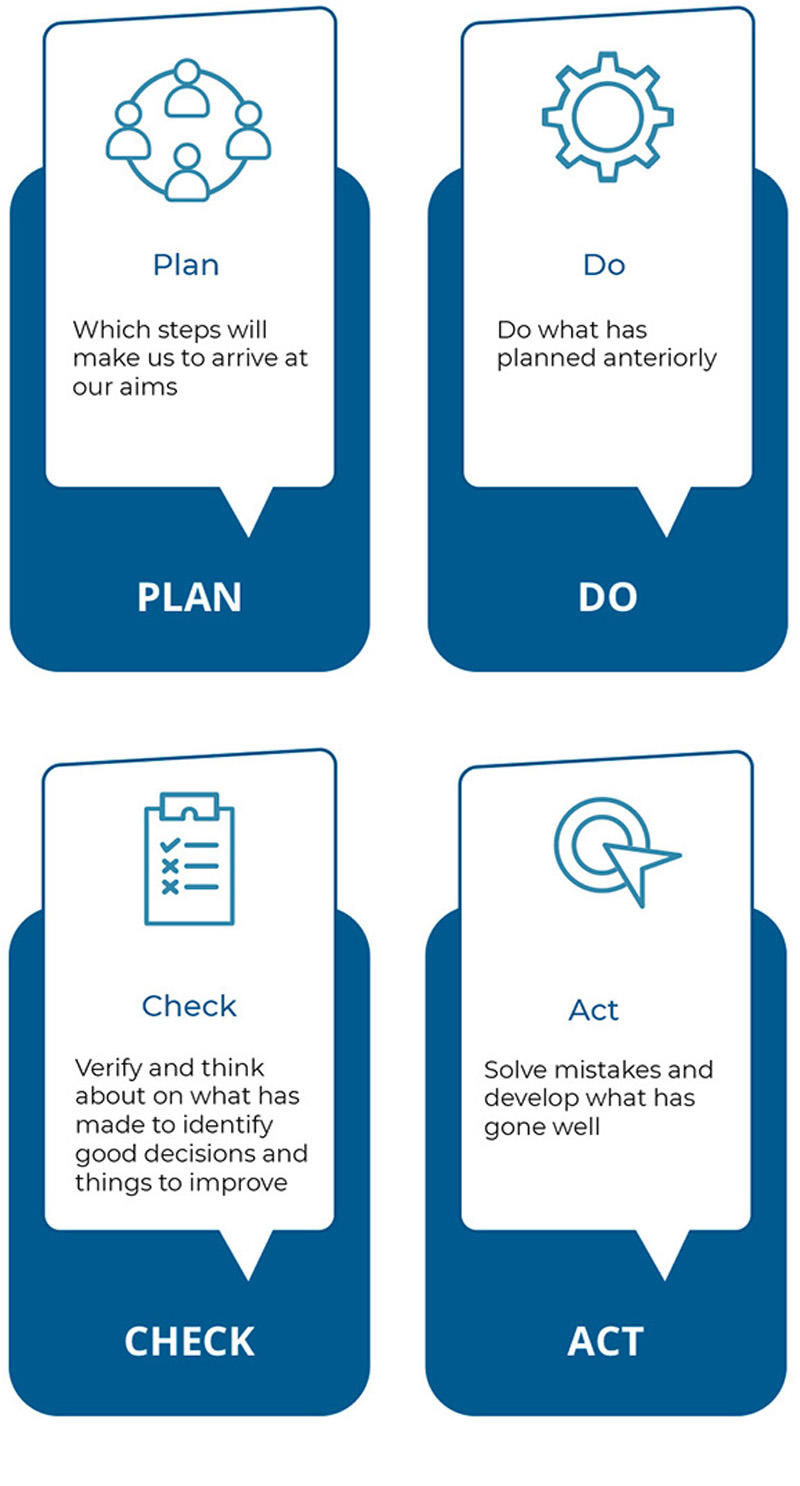
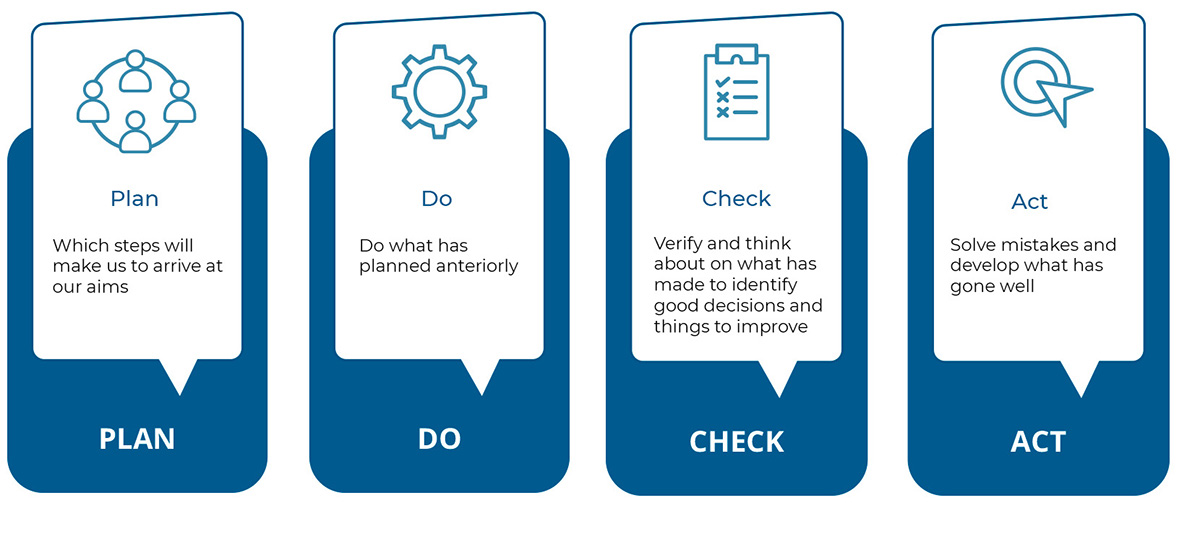
The standard itself is the model for managing digital security company, based on the approach to security as a process and supported by the traditional cycle of continuous improvement Deming: PDCA (Plan - Do - Check - Act).
Evaluation and analysis of technological risk
Analysis and evaluation is performed according to the business plan of each company (Business Plan) and the level of technological risk you are willing to assume.
Development of a Master Plan
.jpg)
We develop a Master Plan for the implementation of security measures.
The Master Plan allows determining the projects to be undertaken by an organization in terms of:
· Its business strategy
· The level of risk that the company wants to take
· The budget allocated to the digital security
· Your specific needs
The projects are sorted according to risk: short, medium and long term, to ensure proper management of information security and prevent incidents materializes.
The Master Plan allows determining the projects to be undertaken by an organization in terms of:
· Its business strategy
· The level of risk that the company wants to take
· The budget allocated to the digital security
· Your specific needs
The projects are sorted according to risk: short, medium and long term, to ensure proper management of information security and prevent incidents materializes.
Monitoring of the implementation of controls and security measures
We advice and monitor the implementation of technological safety measures for reducing the risk of incidents and proper alignment with the business plan of the company.
Awareness and training employees about safety
Awareness and training employees about safety is the most vulnerable point in the safety chain of any company. This is based on ignorance of system users about good security practices.
Development of a digital dashboard security
We develop a digital security Scorecard as to assess the current level of security of the company and the weak points and / or improvement of this security level.

.png)

.png)

![[...]](https://www.complia.es/xtra/imgs/loading.gif)